| FAST BUILD BOXES |
like this
|
| like this |
like this or like this
|
like this
|
shutdown -r -F now and let it reboot.
When it starts back up it will run "fsck" which is the conceptual equivalent
of "chkdsk /f" in the Windows world. Ghost 2003 comes with SystemWorks 2003 or often
comes with motherboard software. Ghost 2003 also works in (the recommended) normal mode
but after the disk is cloned the boot record must be repaired on the cloned drive by
first booting to a rescue disk. Actually, I have had great success using the -ib
(Image Boot) setting. It appears to make an exact duplicate of the boot sector, then
does a regular clone operation on the remainder. There is other software out there that
has the ability to clone Linux hard drives. I’m just used to Ghost.
shutdown -r -F now to repair any potential problems.
|
Make a new directory on your Windows computer and call it 'debian' or
something. Then download the latest version of the Debian installer for 'squeeze' and save
it there. Go to:
http://www.debian.org/releases/squeeze/debian-installer/.
Read the errata while you are on that page. One interesting
errata is
http://bugs.debian.org/cgi-bin/bugreport.cgi?bug=401435. Also note that in version
6.0.0 there are potential installation problems with RTL8169-based network cards. Note that there are squeeze 6.0.6 i386 or squeeze 6.0.6 amd64 (x86-64) CDs available from this location but since I am poor, I have only tested this setup using the i386 CD (32bit). If any of the hardware in your system requires non-free firmware to be loaded with the device driver, you can download a non official image including these non-free firmwares. squeeze 6.0.6 i386 or squeeze 6.0.6 amd64 (x86-64) |
| We are going to erase the hard drive so make sure you don't have any data on it you might need. Make sure the local time is set correctly in BIOS. Boot up the computer using the Installer CD. The instructions below pertain to the default "ask as few questions as possible" mode. When the system boots up to the Debian screen, simply press [Enter] at the Install prompt. |
|
[ !! Select a Language] This determines the language of the installer. This installation has only been tested with English - English [ !! Select your location] Choose what is appropriate. |
| Unplug the ethernet cable so DHCP will fail. |
|
[!! Select a keyboard layout] American English selects a standard qwerty keyboard. |
|
There will be a few screens of activity, then this will come up: [Configuring the network with DHCP] Hit [Cancel] because we want DHCP configuration to fail If it should succeed, choose [Go Back]. |
| Plug the ethernet cable back in. |
|
[!! Configure the network] Network autoconfiguration failed We wanted that to happen, simply press: [Continue] On the next screen, choose the default of: [Configure network manually] |
|
[!! Configure the network] Make sure Num Lock is on! [IP address:]
111.111.111.111
[Netmask:]
255.255.255.x
[Gateway:]
333.333.333.333
[Name server addresses:]
444.444.444.444 555.555.555.555
[Hostname:]
sfa
[Domain name:]
example.com
|
|
[!! Set up users and passwords] This will ask for root's password and allow you to create a "normal" user and a password for that user. Watch your [Num Lock] status. Use really good passwords and don't forget them. Please add one, and just one, normal user here. If you plan on storing mail locally on this machine (not documented here), or even if you don't, create a user who's main purpose in life might be to hold root's mail. I suggest calling the user myroot or something similar. Keep in mind that all the best hacker tools run on Linux. If a hacker gains root access to this box, your entire network is history. |
|
[! Configure the clock] [Select your time zone:] Simply choose what is appropriate. |
|
[! Configure the clock] [Is the system clock set to UTC?] If this comes up it may be an indication the system clock is set to UTC. I prefer to set the system clock to local time so I [tab] over and answer [NO] but this is up to you. |
|
[!! Partition disks] [Partitioning method:] Choose Guided - use entire disk [Select disk to partition:] Choose what is appropriate [Partitioning scheme:] [All files in one partition - (recommended for new users)] [Finish partitioning and write changes to disk] [Write changes to disk?] [Yes] |
|
[Installing the base system] Wait.... |
|
[! Configure the package manager] [Debian archive mirror country:] Choose your country [Debian archive mirror:] Choose a mirror near you (ftp.us.debian.org works very well in the US) [HTTP proxy information] (configure if needed, otherwise leave unconfigured) |
|
[! Configuring popularity contest]
You decide if you would like participate in the package usage survey. |
|
[! Software selection]
[Choose software to install:] This is 'tasksel'. You only want to select 'Standard system utilities' here (nothing else). Use the [spacebar] to deselect 'Graphical desktop environment'. Then, simply [Tab] over and select [Continue]. I heartily recommend you do not run a GUI; however, if you absolutely insist on doing so, leaving 'Graphical desktop environment' selected is the way to install it. |
|
[! Configuring grub-pc] [Install the GRUB boot loader to the master boot record?] Choose [Yes] [!! Finish the installation] The CD door should open, remove the CD, then hit [Continue] This will reboot. |
Once you get the login prompt, login as root and issue the following command:
apt-get install rdate ssh vim
|
Once you are back at the shell prompt, reboot the system with:
reboot
|
| Please install and configure PuTTY and WinSCP per the notes above. |
i",
(short for "insert"). You can edit text pretty much as you would expect in
Write mode. You exit out of Write mode and return to Command mode by hitting
the [Esc] key. There are many commands that can be learned in Command mode but
we only need to learn two more in addition to "i". Those commands
are ":" (a colon) and "/" (a forward slash). The
colon is used to enter the third mode, the Command line mode and the slash
enables the Search command. When you are in Command line mode, you will see a
colon at the bottom of the screen. Here is a list of commands we will use while
in Command line mode:
:q quit (provided you have not made any changes) By the way,
the lower case q is used often in *nix as a way to exit a screen. :q! exits vi and discards changes (great when you trashed the
file and just want to start over!) :wq saves the changes and exits vi (write and quit) :w saves the current changes but does not exit vi (write) G The capital "G" Goes to the bottom of the page (very handy)
/text_to_search_for moves the cursor to the first occurrence of
text_to_search_for
vi /etc/resolv.conf
The file should look something like: search example.com nameserver 444.444.444.444 nameserver 555.555.555.555 Repair it if it is not. (Use "i", then edit it). If you made changes, Exit the file with [Esc] : wqIf you did not need to change anything, Exit the file with [Esc] : q
|
vi /etc/hosts
The top of file should look something like: 127.0.0.1 localhost 111.111.111.111 sfa.example.com sfaRepair it if it does not. Remember, use "i" to insert. Since we are here, you might as well add any other hosts you would like our spamfilter to know about. I suggest you (at least) put your internal mail server(s) here. Simply append any other entries to the bottom of the list. If you made changes, Exit the file with [Esc] : wqIf you did not need to change anything, Exit the file with [Esc] : qIf you have a mess on your hands, Exit the file with [Esc] : q! and try again.
|
We will use rdate to query a couple stratum 2 time servers in order to roughly set
the system clock, then use a script (/etc/init.d/hwclock.sh) that will correct our hardware
clock. We will later install the ntp daemon which will keep the
clock accurate while the system is running. Hopefully at least one of these two servers
will answer our request:
/etc/init.d/hwclock.sh reload
If this process hangs and you get a time out error, it's possible you have a BIOS incompatibility with the hwclock software. This is most common on some Dell machines. If and only if you have a problem here, perform this next step:
sed -i 's/HWCLOCKPARS=/HWCLOCKPARS="--directisa"/' /etc/init.d/hwclock.sh
Continue on:
rdate -4ncv clock.fmt.he.net
|
Earlier I mentioned an errata dealing with tcp_window_scaling. You may want to consider
what may happen (large files fail to transfer between systems) when there
is a buggy router between you and someone else, and may wish to make this change to
the system (you decide):
echo "net.ipv4.tcp_wmem = 4096 65536 65536" >>/etc/sysctl.conf
I am going to assume this may slow down communications between systems under certain circumstances. Here is another setting I have not tried: http://en.wikipedia.org/wiki/TCP_window_scale_option. |
cat /etc/fstab
Copy the contents of the output of this command to a text file and save it on your Windows system. This tells us how drives are mounted. You will need this information should you ever need to boot up in rescue mode. |
Since we are using the squeeze CD, our default system editor will be nano, and not vim.
We soon need to edit a system file called crontab but we don't want to have to learn
another new editor so we will change our default system editor:
update-alternatives --config editor
Choose
/usr/bin/vim.basic
|
If you made changes to any of the above files:
reboot
|
shutdown -h now or poweroff
apt-get update to update the local database of available
packages followed by apt-get upgrade, to install the
latest version of any and all packages it found on our system. This is fine when we
are using the 'stable' version of Debian. If you install 'testing' and
'unstable' versions of some (or all) software, this could spell disaster if we allow
newer packages to be installed indiscriminately. This could make stuff stop
working. Fortunately there is something called "Apt-Pinning" that enables us to
prioritize the order of 'stable', 'testing', and 'unstable' software sources.
The most succinct explanation of this can be found at
http://jaqque.sbih.org/kplug/apt-pinning.html. If you ever use "apt-get upgrade",
I strongly recommend using
apt-get -s upgrade to "simulate" the upgrade process
before you actually upgrade. Make a mental note of this: if you were to have 'testing'
software configured as your top priority, and you were to run 'apt-get upgrade', then
many of your programs will be installed from the 'testing' group of packages. Once this
happens, those packages will continue to update from the 'testing' branch even
if you change your top priority to 'stable'. This action cannot be undone gracefully.
Note that you can prevent any package you want from upgrading
by placing the package on hold.echo "packagename hold" | dpkg --set-selections to
place package 'packagename' on hold and
echo "packagename install" | dpkg --set-selections
to allow it to upgrade. Now, because we will be using a new package repository
called squeeze-updates, we will not be using apt pinning on this box. Upgrades to two of the three programs
we use for fighting spam (SpamAssassin and ClamAV) will be available from squeeze-updates, insuring
that we can upgrade to newer versions without affecting other programs.
apt-get -s install [package]
before you install any package. It lets you "simulate" what would happen. You
will find that apt-cache policy [package] is
also helpful. If you want a package that is an
'unstable' version (or any version that is not top priority), you would have to
specifically request the 'unstable' version or change the priority before you install
it (unless the only version is 'unstable' or your current version is 'unstable').
For example apt-get -t unstable install [package]
will install the package and also satisfy dependencies from 'unstable'.
If you use apt-get install [package]/unstable
then apt will try to meet any dependencies from stable.
If you were to use a tool like tasksel and you want to install from testing or
unstable, you may have to temporarily change the priority prior to installing a
new set of packages. The most stable situation is to only upgrade to new
packages if a security flaw is found and make sure you have the ability to
completely restore the hard drive if upgrades don't go well. So I don't frighten you too
much, the Debian package maintainers are amazing, so apt-get usually works very well.
apt-cache to search the local database for
available packages. apt-cache search [search terms] will find packages that
sound like what you want and: apt-cache show [packagename] will return more details
on a particular package. apt-cache showpkg [packagename] will return more
details on a particular package. apt-cache policy [packagename] will return which
versions are available along with the priority of each version. apt-setup will enable you to change mirrors. The
alternative is to edit /etc/apt/sources.list manually (which I prefer). apt-get clean clears the local repository of all retrieved
package files. apt-get autoclean clears the local repository of retrieved
package files of programs that are no longer installed. dpkg -l [packagename] will list the version and a short
description of the package we have installed.
cp /etc/apt/sources.list /etc/apt/sources.backup
This creates a backup file. Then:
vi /etc/apt/sources.list
|
At this point, the contents of the file may look something like this:
# deb cdrom:[Debian GNU/Linux 6.0.0 _Squeeze_ - Official i386 NETINST Binary-1 20110205-14:34]/ squeeze main #deb cdrom:[Debian GNU/Linux 6.0.0 _Squeeze_ - Official i386 NETINST Binary-1 20110205-14:34]/ squeeze main deb http://ftp.us.debian.org/debian/ squeeze main deb-src http://ftp.us.debian.org/debian/ squeeze main deb http://security.debian.org/ squeeze/updates main deb-src http://security.debian.org/ squeeze/updates main deb http://ftp.us.debian.org/debian/ squeeze-updates main deb-src http://ftp.us.debian.org/debian/ squeeze-updates main We need to modify this file so the result will look something like this: (with only the http server unique to your particular system) deb http://ftp.us.debian.org/debian/ squeeze main non-free deb-src http://ftp.us.debian.org/debian/ squeeze main deb http://security.debian.org/ squeeze/updates main non-free deb-src http://security.debian.org/ squeeze/updates main deb http://ftp.us.debian.org/debian/ squeeze-updates main deb-src http://ftp.us.debian.org/debian/ squeeze-updates main |
apt-get update
|
echo 'APT::Cache-Limit "25165824";' >> /etc/apt/apt.conf
|
less. less is a great file
and directory viewer.
less.less:less /path/file
less:ls -l | less (current directory, or)
ls -l /path/directory | less
history | less
locate.
locate allows you to search a database of every file name on the system.
It's kind of like Windows Find. You first have to build the database with the
updatedb command, and then you can search through it.
locate and less
together:
updatedb
locate keymaps | less
less
/lib/udev/keymaps
cd
cd and hit [return]. We just saved ourselves
having to type the entire path name just in order to change to that directory.
I like that.
cd to get back home.
iptables -F
|
iptables -L
|
vi /etc/network/interfaces
And insert the following text (remember, it's "i" to insert) in the blank line just below "iface lo inet loopback":
pre-up iptables-restore < /etc/firewall-rules
Save and exit the file as usual with [Esc] : wq From now on I will assume you know how to edit, save, and exit files using vi. If not stated, it will be implied that after editing a file, you need to save and exit it, or if necessary, discard changes and start over. |
If you have not done so, reboot again and runiptables -L to verify the firewall loaded during start up. |
iptables -F from the
console to clear out iptables. This will allow you another shot at it.
top (once in 'top', it's q to exit. You can sort using > or <
ps afx
ps afxl
ps aux
ps -A
ls -F /etc/rc2.d
lsof -i | grep LISTEN
lsof -P | grep LISTEN
netstat -pn -l -A inet
netstat -pn -l inet
cp -r /etc/init.d /etc/init.d-original
|
/etc/init.d/nfs-common stop
|
lsof -i | grep LISTEN
The only daemon you should see is at this point is *:ssh If there are other programs shown, try rebooting and test again. |
update-rc.d nfs-common defaults
/etc/init.d/nfs-common start
cp -i /etc/init.d-original/nfs-common /etc/init.d
update-rc.d nfs-common defaults
/etc/init.d/nfs-common start
We will save the time to the real-time clock once each day:
crontab -e
and insert on the first available blank line (after all the comments!):
11 11 * * * /etc/init.d/hwclock.sh reload >/dev/null
Then save and exit the file.
Change the default shell from dash to bash:
dpkg-reconfigure dash
Answer: Use dash as the default system shell (/bin/sh)? <No> |
apt-get install libmime-perl libarchive-zip-perl libberkeleydb-perl libcompress-raw-zlib-perl libcompress-zlib-perl libconvert-binhex-perl libconvert-tnef-perl libconvert-uulib-perl libio-compress-base-perl libio-compress-zlib-perl libio-multiplex-perl libio-stringy-perl libmailtools-perl libmime-tools-perl libnet-cidr-perl libnet-server-perl libtimedate-perl libunix-syslog-perl
And there are more:
apt-get install libcrypt-openssl-bignum-perl libcrypt-openssl-rsa-perl libdigest-hmac-perl libdigest-sha1-perl liberror-perl libmail-dkim-perl libnet-dns-perl libnet-ip-perl pax libmysqlclient16 libpq5 mysql-common ssl-cert libimage-info-perl libdbd-mysql-perl libnet-cidr-lite-perl
And there are more:
apt-get install ntp clamav clamav-daemon clamav-freshclam lha arj zoo nomarch lzop cabextract libnet-ldap-perl libauthen-sasl-perl libdbi-perl p7zip rpm unrar-free libsnmp-perl libmail-spf-perl libnetaddr-ip-perl libsys-hostname-long-perl make re2c dnsutils
And there are more:
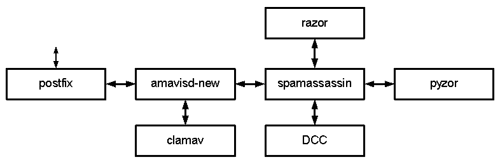
apt-get install gcc-4.4-locales gcc-multilib autoconf automake1.9 libtool flex bison gdb gcc-4.4-multilib libmudflap0-4.4-dev gcc-4.4-doc libgcc1-dbg libgomp1-dbg libmudflap0-dbg libcloog-ppl0 libppl-c2 libppl7 razor libnet-ident-perl libio-socket-ssl-perl pyzor libencode-detect-perl
|
First, run a simulation:
apt-get -s upgrade
Then if everything is as you might expect:
apt-get upgrade
|
If the kernel is upgraded, once the upgrade process is complete, you must:
reboot
|
apt-cache policy postfix spamassassin
|
spamassassin:
Installed: (none)
Candidate: 3.3.1-1
Version table:
3.3.1-1 0
500 http://ftp.us.debian.org/debian/ squeeze/main i386 Packages
postfix:
Installed: (none)
Candidate: 2.7.1-1
Version table:
2.7.1-1 0
500 http://ftp.us.debian.org/debian/ squeeze/main i386 Packages
This tells us that the squeeze version of Postfix will be installed
and the squeeze version of SpamAssassin will be installed.
If we wanted to install a testing version of a program (for example), we would
have to override the choices we make when we use apt-get, e.g. apt-get
install [packagename]/testing, or if necessary
apt-get -t testing install [packagename]. Note
that another option would be to momentarily make testing the highest priority in
/etc/apt/preferences, then override what will be installed, e.g.
apt-get install [packagename]/testing.
Read this.
At this time however, we are not using apt pinning. Since we are using squeeze-updates,
we would be able to upgrade SpamAssassin (when an upgrade is available) by simply installing it.
Remember that it's a good idea to simulate an installation first (using the -s switch).
There is a Debian version of amavisd-new available, but are NOT
going to install it. The configuration files for Debian versions of amavisd-new are
not consistent with the typical way amavisd-new is configured. Instead of one
configuration file, the newer Debian versions split the configuration files into half
a dozen files in a couple different directories. We will instead install amavisd-new
from the original author. Also, by NOT installing the Debian version, it will be easier to upgrade amavisd-new.
So with this in mind:
apt-get install spamassassin
If you install 3.3.1 and want to prevent accidental upgrades (via squeeze-updates), one option is to place the package on hold:
echo "spamassassin hold" | dpkg --set-selections
|
We have to make sure this is not installed:
apt-get remove libio-socket-inet6-perl
|
apt-get install postfix postfix-pcre postfix-mysql postfix-ldap
|
|
Debconf will pop up a Postfix configuration screen. For [General type of configuration?] select the default of: Internet Site For System mail name: tab over and select [Ok] to accept the default sfa.example.com |
If (and only if) you already have amavisd-new installed, you need to remove it
(this will not remove your configuration files which is a good thing). First make
sure amavisd-new is the only thing that will be removed by 'simulating' the removal:
apt-get -s remove amavisd-new
If it is, then remove it:
apt-get remove amavisd-new
If it is not, then you must make a note of any and all programs that will be removed, because you will have to reinstall them. Good luck with all that. ;)
|
There may be complaints that some things do not exist and other things
already exist. This should not be a problem.
adduser --group --system --home /var/lib/amavis --shell /bin/sh amavis
Now, very important, add the clamav user to the amavis group, then restart clamd:
gpasswd -a clamav amavis
|
cd /usr/local/src
Change these next lines to match the (author's) version of Postfix you have (hint: dpkg -l postfix ):
wget http://ftp.debian.org/debian/pool/main/p/postfix/postfix_2.7.1.orig.tar.gz
|
ls -l
|
| The line below may need to be edited if your version of the Postfix
source code is different than mine. MAKE SURE you answer "n" to "overwrite?" Do each section separately.
cp -i /usr/local/src/postfix-2.7.1/conf/* /etc/postfix
|
The master.cf we download here can be used with recent Postfix versions.
postfix stop
|
postfix stop
|
| Add these lines near the bottom of master.cf. The "-o" is the lower case letter o, not zero. These settings are from http://www.ijs.si/software/amavisd/README.postfix.old. You can copy and paste this entire section once the cursor is in the correct position (see below) and you are in insert mode. Note: rather than using a right click of the mouse to paste into the editor, you can also use [Shift]+[Insert]. Actually, I suggest using the WinSCP editor here: |
smtp-amavis unix - - n - 2 smtp
-o smtp_data_done_timeout=1200
-o smtp_send_xforward_command=yes
-o disable_dns_lookups=yes
-o max_use=20
127.0.0.1:10025 inet n - n - - smtpd
-o content_filter=
-o smtpd_delay_reject=no
-o smtpd_client_restrictions=permit_mynetworks,reject
-o smtpd_helo_restrictions=
-o smtpd_sender_restrictions=
-o smtpd_recipient_restrictions=permit_mynetworks,reject
-o smtpd_data_restrictions=reject_unauth_pipelining
-o smtpd_end_of_data_restrictions=
-o smtpd_restriction_classes=
-o mynetworks=127.0.0.0/8
-o smtpd_error_sleep_time=0
-o smtpd_soft_error_limit=1001
-o smtpd_hard_error_limit=1000
-o smtpd_client_connection_count_limit=0
-o smtpd_client_connection_rate_limit=0
-o receive_override_options=no_header_body_checks,no_unknown_recipient_checks,no_milters
-o local_header_rewrite_clients=
|
Add this just below the 'pickup' service type:
-o content_filter=
-o receive_override_options=no_header_body_checks |
# ==========================================================================
# service type private unpriv chroot wakeup maxproc command + args
# (yes) (yes) (yes) (never) (100)
# ==========================================================================
smtp inet n - - - - smtpd
#submission inet n - - - - smtpd
# -o smtpd_tls_security_level=encrypt
# -o smtpd_sasl_auth_enable=yes
# -o smtpd_client_restrictions=permit_sasl_authenticated,reject
# -o milter_macro_daemon_name=ORIGINATING
#smtps inet n - - - - smtpd
# -o smtpd_tls_wrappermode=yes
# -o smtpd_sasl_auth_enable=yes
# -o smtpd_client_restrictions=permit_sasl_authenticated,reject
# -o milter_macro_daemon_name=ORIGINATING
#628 inet n - - - - qmqpd
pickup fifo n - - 60 1 pickup
-o content_filter=
-o receive_override_options=no_header_body_checks
cleanup unix n - - - 0 cleanup
qmgr fifo n - n 300 1 qmgr
#qmgr fifo n - - 300 1 oqmgr
tlsmgr unix - - - 1000? 1 tlsmgr
rewrite unix - - - - - trivial-rewrite
bounce unix - - - - 0 bounce
defer unix - - - - 0 bounce
trace unix - - - - 0 bounce
verify unix - - - - 1 verify
flush unix n - - 1000? 0 flush
proxymap unix - - n - - proxymap
proxywrite unix - - n - 1 proxymap
smtp unix - - - - - smtp
# When relaying mail as backup MX, disable fallback_relay to avoid MX loops
relay unix - - - - - smtp
-o smtp_fallback_relay=
# -o smtp_helo_timeout=5 -o smtp_connect_timeout=5
showq unix n - - - - showq
error unix - - - - - error
retry unix - - - - - error
discard unix - - - - - discard
local unix - n n - - local
virtual unix - n n - - virtual
lmtp unix - - - - - lmtp
anvil unix - - - - 1 anvil
scache unix - - - - 1 scache
# Interfaces to non-Postfix software not shown in this example
smtp-amavis unix - - n - 2 smtp
-o smtp_data_done_timeout=1200
-o smtp_send_xforward_command=yes
-o disable_dns_lookups=yes
-o max_use=20
127.0.0.1:10025 inet n - n - - smtpd
-o content_filter=
-o smtpd_delay_reject=no
-o smtpd_client_restrictions=permit_mynetworks,reject
-o smtpd_helo_restrictions=
-o smtpd_sender_restrictions=
-o smtpd_recipient_restrictions=permit_mynetworks,reject
-o smtpd_data_restrictions=reject_unauth_pipelining
-o smtpd_end_of_data_restrictions=
-o smtpd_restriction_classes=
-o mynetworks=127.0.0.0/8
-o smtpd_error_sleep_time=0
-o smtpd_soft_error_limit=1001
-o smtpd_hard_error_limit=1000
-o smtpd_client_connection_count_limit=0
-o smtpd_client_connection_rate_limit=0
-o receive_override_options=no_header_body_checks,no_unknown_recipient_checks,no_milters
-o local_header_rewrite_clients=
|
/etc/postfix/main.cf the main
configuration file for Postfix. Following are suggested values to use in
main.cf. These have been tested for this configuration and will work fine, but
there are many judgment calls involved in this, and it is a good idea at some
point to learn more about Postfix configuration on your own. You could first
look at the sample Postfix main.cf file /usr/share/postfix/main.cf.dist
. There are comments describing some of the most common options.
Refer also to the Postfix documents on your machine in the
/usr/local/src/postfix-2.7.1/README_FILES directory, or
read the documentation on the Postfix web site
http://www.postfix.org/documentation.html. I also recommend
http://www.postfix-book.com/.
postmap
command to create binary files (Berkeley DB format) that Postfix will ultimately use to
retrieve the data. For example, if you have a file called "filename" and you "postmap filename",
a new file is created "filename.db". When we reference the file as data type "hash:", Postfix will
retrieve data from "filename.db", not "filename".
There are more than a dozen other types of data files that Postfix
can use to store data. Hash tables are an appropriate choice for
several tables we will use, and pcre (Perl Compatible Regular Expressions)
is appropriate for a couple tables we will use to hold content filtering data.
In its simplest form a hash table is comprised of 2 pieces of data,
a key and a value; typically referred to as the key/value pair. The key
and the value are separated with whitespace (typically a space or tab).
The data in a typical table that we use in Postfix would look something like:
postconf -e "alias_maps = hash:/etc/aliases"
|
newaliases now, and every time after you edit the aliases file. The
newaliases command is just like postmap except that it's
specific to the aliases file.
newaliases
|
postconf -e "myorigin = example.com"
|
postconf -e "myhostname = sfa.example.com"
|
Please read important notes above.
postconf -e "mynetworks = 127.0.0.0/8, 192.168.1.0/24, 222.222.222.222/24, 10.10.10.10/24"
|
postconf -e "message_size_limit = 10485760"
|
postconf -e "local_transport = error:no local mail delivery"
|
postconf -e "mydestination = "
|
postconf -e "local_recipient_maps = "
|
postconf -e "smtpd_use_tls=no"
|
Set up a reference to the virtual file:
postconf -e "virtual_alias_maps = hash:/etc/postfix/virtual"
Then edit the virtual file:
vi /etc/postfix/virtual
and add postmaster and admin in the format:
postmaster postmaster@example.com
Save and exit the file, then create the binary file that Postfix will use:
postmap /etc/postfix/virtual
|
Read the notes above before you enter this:
postconf -e "relayhost = [666.666.666.666]"
|
Set up a reference to a file we will create to store the data:
postconf -e "relay_recipient_maps = hash:/etc/postfix/relay_recipients"
Then edit that file:
vi /etc/postfix/relay_recipients
For the moment, we are going to accept mail for all users in our domain(s) so enter each domain you accept mail for in the format:
@example.com OK
Then create the binary file that Postfix will use:
postmap /etc/postfix/relay_recipients
The entries above are temporary. They are wildcards that allow mail to your domains. You MUST remove the entries above at some point in the near future and replace them with every single one of your valid recipients' email addresses. When you are ready to enter each user individually in the relay_recipients file, you would first remove (or comment out) the data above that allows mail to all users in the domain, and then list each user individually in the form:
user1@example.com OK
|
/etc/postfix/transport and we
will set it up in similar fashion to relay_recipients.
Create a reference to it in main.cf:
postconf -e "transport_maps = hash:/etc/postfix/transport"
Then edit it:
vi /etc/postfix/transport
Add 1 new line for each domain for which you will be handling mail, similar to the example below. The IP address is that of whatever server is the final destination of messages addressed to our domain(s) (our Exchange server). It does not matter where you place these items in the file, but I like to put them at the top.
example.com relay:[666.666.666.666]
(DO include the brackets on these lines. You can also use a FQDN hostname instead of an IP address (i.e. relay:[exchange.example.com]). Then create the binary file Postfix will use:
postmap /etc/postfix/transport
|
postconf -e "relay_domains = example.com, example2.com, example3.com"
|
recipient_delimiter
should be set to match the delimiter you are currently using to
separate the user name from the address extension. Amavisd-new
also uses $recipient_delimiter and this setting needs to match the
Postfix setting. This has nothing to do with the comma you are using to separate
multiple people you send email to (user1@example.com, user2@example.com, user3@example.com)
using your email client (MUA).
|
Typical settings - Choose one I Don't use recipient delimiters:
postconf -e "recipient_delimiter = "
I currently use the plus sign:
postconf -e "recipient_delimiter = +"
I currently use the minus sign:
postconf -e "recipient_delimiter = -"
|
If (and only if) the IP address you present to the world is not the IP
address of your spamfilter (you are configured to run behind a NAT firewall
or a proxy server) please vi /etc/postfix/main.cf and add these two lines to main.cf, then you must
uncomment and configure proxy_interfaces (1.2.3.4 represents the public
IP address):
# Specify your NAT/proxy EXTERNAL address here.
|
Address rewriting. When using a content_filter like amavisd-new,
because mail is sent to Postfix twice, address rewriting takes place twice unless we
disable it either before amavisd-new or after amavisd-new has processed a message. Our
virtual file is one example of a table that rewrites addresses. We will disable
rewriting by placing 'no_address_mappings' in a 'receive_override_options' override
in master.cf. It is up to you
to decide whether you want amavisd-new to see the original address, or the rewritten
address. I find it preferable to disable rewriting prior to amavisd-new.
In master.cf you can disable address rewriting before amavisd-new by
setting:
smtp inet n - - - - smtpd
-o receive_override_options=no_address_mappings
Be careful, there are two lines that look similar. You are looking
for smtpd on the right hand side. To instead disable address rewriting when amavisd-new
returns (non discarded) messages to Postfix, you would edit the current receive_override_options
override on the reinjection port (127.0.0.1:10025). For example, if we now have:
127.0.0.1:10025 inet n - - - - smtpd
[...lots of overrides are here...]
-o receive_override_options=no_header_body_checks,no_unknown_recipient_checks,no_milters
You would change this to:
127.0.0.1:10025 inet n - - - - smtpd
[...lots of overrides are here...]
-o receive_override_options=no_address_mappings,no_header_body_checks,no_unknown_recipient_checks,no_milters
vi /etc/postfix/master.cf
and edit one or the other.
|
postconf -e "smtpd_helo_required = yes"
|
SMTP session
|
V
restriction stage-------------
test ---------------REJECT->
| \
| DUNNO
| \
| V
| next test------REJECT->
| | \
OK OK DUNNO
| | \
V V V
next restriction stage-------
|
postconf -e "smtpd_sender_restrictions = check_sender_access hash:/etc/postfix/sender_access, reject_non_fqdn_sender, reject_unknown_sender_domain"
|
postconf -e "smtpd_recipient_restrictions = permit_mynetworks, reject_unauth_destination"
|
postconf -e "smtpd_data_restrictions = reject_unauth_pipelining"
|
/^Received: from localhost \(localhost\.localdomain \[127\.0\.0\.1\]\)/ IGNORE -o receive_override_options=no_header_body_checks,no_unknown_recipient_checks
Optional (only use if you intend on using header_checks):
postconf -e "header_checks = pcre:/etc/postfix/header_checks"
|
Optional (only use if you intend on using body_checks):
postconf -e "body_checks = pcre:/etc/postfix/body_checks"
|
postconf -e "content_filter = smtp-amavis:[127.0.0.1]:10024"
|
vi /etc/postfix/sender_access
|
#Example sender access map file
makeabuck@mlm.tld 550 No MLM thanks
allspam.tld 550 Spam is not accepted here
badguy.net REJECT
justaspamminfool@allspamallthetime.com REJECT
newsletter-fake-domain.com OK
my-bogus-test-domain.com OK
postmap /etc/postfix/sender_access
|
vi /etc/postfix/main.cf
Check the contents of the file for errors and repair if needed. You will probably want to edit relay_domains and mynetworks. |
postfix start
|
telnet 127.0.0.1 25
You should see: 220 sfa.example.com ESMTP Postfix (Debian/GNU) hit [enter] a couple times; then type:
quit
to exit |
postfix stop). Make sure you ran newaliases
and all the postmap commands above. Check all the settings in main.cf and master.cf.
Begin debugging by checking the mail.log for a fatal error: grep fatal /var/log/mail.log
There is a nice paper on troubleshooting Postfix at
http://www.postfix-book.com/debugging.html but keep in mind our system is not
ready to relay mail at this point (it will end up in the queue because we
have not yet configured amavisd-new).
postfix reload
|
cd p then hit the [tab] key and
the bash shell will fill the remainder in with the first unambiguous item. If there
is more than one item, you can hit the [tab] key twice and it will list all the available
items.cd p[tab] e[tab]
c[tab][enter]
cd /usr/local/src
This next line may be edited for a different version of postfix:
cd postfix-2.7.1/examples/chroot-setup
postfix stop
You can check if Postfix is happy:
postfix check
|
cp /etc/amavis/amavisd.conf /etc/amavis/amavisd.conf-2.6.6-original
|
Either:
vi /etc/amavis/amavisd.conf
or use the WinSCP editor to edit this file (recommended). Locate the line that begins with $mydomain:
$mydomain = 'example.com';
and change to reflect the actual name of this system's domain. Next, uncomment # $myhostname and change it to our host's FQDN:
$myhostname = 'sfa.example.com';
Locate this next line:
@local_domains_maps = ( [".$mydomain"] );
Comment out that line, then add a new one just like it with all your domains listed in it. Like this:
@local_domains_maps = ( [ ".$mydomain", '.example2.com', '.example3.com' ] );
Or like this:
@local_domains_maps = ( [qw( .example.com .example2.com .example3.com )] );
The periods in front of the domains are wildcards for subdomains (or hosts). Don't forget the semi-colon at the end. Note that in Perl, single quotes and double quotes work differently from each other. Just below this is @mynetworks, which should be edited to include our network (provided our network is not included in one of the RFC 1918 ranges already configured here): @mynetworks = qw( 127.0.0.0/8 [::1] [FE80::]/10 [FEC0::]/10
10.0.0.0/8 172.16.0.0/12 192.168.0.0/16 222.222.222.222/24);
|
Change
$sa_tag_level_deflt = 2.0;
to
$sa_tag_level_deflt = undef;
This will insure all mail addressed to domains in @local_domains will get a spam score in the header, spam or not. Change
$sa_tag2_level_deflt = 6.31;
to
$sa_tag2_level_deflt = 5.0;
This low number is assuming your email clients do not automatically discard spam. Set this to 8.0 or higher if they do. The Subject line will be prepended with "Spam> " for any mail that scores above $sa_tag2_level_deflt and is passed to a recipient. Change
$sa_kill_level_deflt = 6.31;
to
$sa_kill_level_deflt = 8.0;
On our system, this will trigger the spam to be quarantined if it scores 8.0 or higher. If you only want spam tagged and sent to the recipients (not quarantined at all), set this to 9999 (this would be for ISPs and large companies that configure MUAs or LDAs to further process spam). |
/etc/cron.d/amavisd-new and
/etc/cron.daily/amavisd-new.
Note that when these cron jobs are running, the Bayes files will at times be
inaccessible. If you happen to see in a log file that SpamAssassin has timed out,
this could be one possible reason.
Now find:
$virus_admin = "postmaster\@$mydomain";
The default is fine, but you may wish to change it. Now add a line for banned file notifications:
$banned_admin = "postmaster\@$mydomain";
|
Next, locate this section:
$mailfrom_notify_admin = "virusalert\@$mydomain"; $mailfrom_notify_recip = "virusalert\@$mydomain"; $mailfrom_notify_spamadmin = "spam.police\@$mydomain";and change it to: $mailfrom_notify_admin = "postmaster\@$mydomain"; $mailfrom_notify_recip = "postmaster\@$mydomain"; $mailfrom_notify_spamadmin = "postmaster\@$mydomain";Just below this, remove the '# ' to uncomment this line:
# $hdrfrom_notify_sender = "amavisd-new <postmaster\@$mydomain>";
|
Next, locate # $recipient_delimiter. You set recipient_delimiter
in Postfix and the setting in this file needs to be set similarly. This is
typically set to one of these three options:
$recipient_delimiter = '';
# No recipient delimiter (this is the default)or
$recipient_delimiter = '+';
or
$recipient_delimiter = '-';
Change:
$sa_spam_subject_tag = '***SPAM*** ';
to
$sa_spam_subject_tag = 'Spam> ';
The longer version simply takes up too much real estate on the subject line. |
The next line I would like to change begins with:
$final_banned_destiny = D_BOUNCE;
Change this to:
$final_banned_destiny = D_DISCARD;
The next line I would like to change begins with:
$final_spam_destiny = D_BOUNCE;
Change this to:
$final_spam_destiny = D_DISCARD;
|
$spam_quarantine_to = undef;
and the email with a SpamAssassin score of 12 or higher would evaporate
into thin air, or you could alternately leave $sa_kill_level_deflt at something like 8 and
set $sa_quarantine_cutoff_level = 12; (preferably higher - I use 14).
But don't do this; at least not yet. Setting
$spam_quarantine_to = undef; essentially
means "we don't have a spam quarantine area so I guess I have to just dump the
mail". This is something you probably should not implement at first; at least not if you
enjoy being employed.
If you decide to do this, I suggest you wait
a month or so to get a feel for the system (and let the
Bayes
database initialize). You can eliminate about
90% of the email that ends up in the "spambin" by using this suggestion.
Next, locate the line that looks like this:
$virus_quarantine_to = 'virus-quarantine';
I suggest you do one of three things here. You can leave this alone, and viruses will be quarantined on the spamfilter box (to /var/lib/amavis/virusmails), or you can set this to:
$virus_quarantine_to = undef;
and provided we configure a virus scanner, all caught viruses will disappear, or you can send caught viruses to a regular mailbox:
$virus_quarantine_to = "virii\@$mydomain";
You can choose to use "spambin" for the quarantine area for all spam, viruses and email with banned attachments, but I recommend you create separate mailboxes for each, virii, spambin and banned. |
Next, locate the $banned_quarantine_to line and configure these
three lines in this manner (remember to use double quotes when variables are involved):
$banned_quarantine_to = "banned\@$mydomain";
Make sure you have mailboxes for these two addresses on a destination server. This is where you will review quarantined email, and if ham is found, will forward the ham to the proper recipient. Locate this section and uncomment the qr'^MAIL$', line (if it is currently commented out): @keep_decoded_original_maps = (new_RE( # qr'^MAIL$', # retain full original message for virus checking (can be slow) Locate this block inside the $banned_filename_re = new_RE section: qr'.\.(exe|vbs|pif|scr|cpl)$'i, # banned extension - basic # qr'.\.(exe|vbs|pif|scr|cpl|bat|cmd|com)$'i, # banned extension - basic+cmd # qr'.\.(ade|adp|app|bas|bat|chm|cmd|com|cpl|crt|emf|exe|fxp|grp|hlp|hta| # inf|ins|isp|js|jse|lnk|mda|mdb|mde|mdw|mdt|mdz|msc|msi|msp|mst| # ops|pcd|pif|prg|reg|scr|sct|shb|shs|vb|vbe|vbs| # wmf|wsc|wsf|wsh)$'ix, # banned ext - long # qr'.\.(ani|cur|ico)$'i, # banned cursors and icons filename # qr'^\.ani$', # banned animated cursor file(1) typeIf you would like to greatly extend the types of attachments amavisd-new bans, you might want to comment out, and uncomment some lines like so: # qr'.\.(exe|vbs|pif|scr|cpl)$'i, # banned extension - basic
qr'.\.(exe|vbs|pif|scr|cpl|bat|cmd|com)$'i, # banned extension - basic+cmd
qr'.\.(ade|adp|app|bas|bat|chm|cmd|com|cpl|crt|emf|exe|fxp|grp|hlp|hta|
inf|ins|isp|js|jse|lnk|mda|mdb|mde|mdw|mdt|mdz|msc|msi|msp|mst|
ops|pcd|pif|prg|reg|scr|sct|shb|shs|vb|vbe|vbs|
wmf|wsc|wsf|wsh)$'ix, # banned ext - long
qr'.\.(ani|cur|ico)$'i, # banned cursors and icons filename
qr'^\.ani$', # banned animated cursor file(1) type
Just edit out the attachment types you would like to receive or edit in
any others you would like to ban. Each vertical bar means "alternately". I would
add bin|drv|mht|ocx|ovl If you receive
mail from people using Outlook in Rich Text mode, make sure you
don't block |tnef When an email that has one of these attachments comes into the system, the entire message gets placed in quarantine and the sender and postmaster get notified. Using this feature of amavisd-new goes a very long way toward preventing email borne viruses from entering your network. This method should not be your only line of defense however, just another tool in your arsenal. |
Next, locate the # ENVELOPE SENDER SOFT-WHITELISTING / SOFT-BLACKLISTING section. |
Locate the line:
@av_scanners = (
Uncomment these 4 lines, and make sure the value after CONTSCAN reads as follows: ['ClamAV-clamd',
\&ask_daemon, ["CONTSCAN {}\n", "/var/run/clamav/clamd.ctl"],
qr/\bOK$/, qr/\bFOUND$/,
qr/^.*?: (?!Infected Archive)(.*) FOUND$/m ],Save
the file with [Esc]:wq and exit vi. Then
make a backup:
cp /etc/amavis/amavisd.conf /etc/amavis/amavisd.conf-03Mar11
I have a habit of using the date for my backups. |
$max_servers = 2;$max_servers = 4;
smtp-amavis unix - - - - 2 smtp
smtp-amavis unix - - - - 4 smtp
Optionally disable logging to /var/log/mail.info:
vi /etc/rsyslog.conf
and comment out the mail.info line, like so: #mail.info -/var/log/mail.info |
|
Optional: If you would like to enable the external template files (located in /etc/amavis/en_US/) so you may customize them in the future (English only):
vi /etc/amavis/amavisd.conf
and uncomment the line:
# read_l10n_templates('en_US', '/etc/amavis');
|
amavisd-new stop
|
| Use the [Ctrl]+c key combination to exit (kill) amavisd-new debug. |
We need to apply a small patch to pyzor:
cd /usr/bin
Here we supply the hostname of the Pyzor server to Pyzor (for both the 'root' and 'amavis' users). This will create a .pyzor directory in both user's home directories, and place the server's hostname in a 'servers' file therein:
pyzor discover
Test the pyzor server for a response:
pyzor ping
Pyzor Ping should show 'OK'. If not, then it's possible your firewall is blocking udp replies from 82.94.255.100 or 188.40.77.236 (public.pyzor.org port 24441), or the server may simply be slow to respond (often the case). I suggest you subscribe to http://lists.sourceforge.net/lists/listinfo/pyzor-announce. |
You will need a sample spam to feed to spamassassin:
cd /var/lib/amavis
|
amavisd-new -d config debug-sa you would notice that amavis
expects to find programs and configuration files in certain places. If you were to run
spamassassin -D config </var/lib/amavis/sample-spam.txt as root you would notice that
root expects to find the same things, but it expects to find some of them
somewhere other than where the amavis user expects. SpamAssassin is designed to enable each
user to have their own settings and data. This section will make both users happy,
and the reason we want to do this is because if we are debugging SpamAssassin
or Razor or Pyzor or DCC, we want to be able to do so with
spamassassin -D </var/lib/amavis/sample-spam.txt rather than amavisd-new -d 5 debug-sa
because we don't want to shut amavisd-new down every time we need to debug one of
those programs. A better way to debug SpamAssassin is to run the program as the
amavis user like so: su amavis -c 'spamassassin -D </var/lib/amavis/sample-spam.txt'
spamassassin -D </var/lib/amavis/sample-spam.txt
|
cp -ir /root/.spamassassin /root/.spamassassin-backup
Please answer 'n' to "overwrite?":
cp -ir /root/.spamassassin /var/lib/amavis
|
rm /root/.spamassassin/user_prefs
|
sa-learn --force-expire
or spamassassin --lint -D or other
spamassassin commands from the root
account, SpamAssassin may change the owner of the Bayes files to 'root'.
If it does, amavis will no longer be able to read those files.
You would need to run
chown -R amavis:amavis /var/lib/amavis
to regain ownership.
In general, if you do any spamassassin maintenance from the
command prompt as root, the best thing to do is run
chown -R amavis:amavis /var/lib/amavis afterwards;
just to make sure.
You can avoid these problems by remembering to run
spamassassin commands as the amavis user. For example
su amavis -c 'sa-learn --sync --force-expire'
cd
If you get an error, you may need to run the 'razor-admin register' command more than once. Don't worry about it if /etc/razor/razor-agent.conf does not exist. Now edit root's razor configuration file:
vi /root/.razor/razor-agent.conf
and change the line:
debuglevel = 3
to:
debuglevel = 0
Obviously -zero- not -oh-; Save and exit the file. OK, now copy root's .razor directory and files to the amavis user's home directory:
cp -r /root/.razor /var/lib/amavis
|
vi /etc/spamassassin/local.cf
And insert the lines:
bayes_path /var/lib/amavis/.spamassassin/bayes
This insures both the root and amavis users use the same files and do not have to guess where they are, and whitelists our spambin. lock_method flock is used
when the Bayes data resides on the local hard disk and is non NFS.
Optional: Since there is a script that runs each day to --force-expire old Bayes tokens "/etc/cron.daily/amavisd-new" (make sure there is if you use this setting!), we can set:
bayes_auto_expire 0
Optional: We will normally have DNS available:
dns_available yes
Possibly optional, possibly not: Depending on your setup, it might be necessary to explicitly set internal_networks and trusted_networks. The trust path tells spamassassin which clients are not trusted. If you are using SpamAssassin version 3.2 or newer, do not include the 127/8 networks shown below. They are automatically included. See http://wiki.apache.org/spamassassin/TrustPath and this thread:
# explicitly set our internal_networks (might be the same or similar to mynetworks)
|
With SpamAssassin version 3.1 or newer, additional configuration is needed:
vi /etc/spamassassin/v310.pre
To enable the ability to use DCC, uncomment the line:
#loadplugin Mail::SpamAssassin::Plugin::DCC
|
Since we are using SpamAssassin 3.1.1 or greater
we can use the new sa-update feature:
sa-update
You should find the new rules in /var/lib/spamassassin/<SA version>. You should also run amavisd-new -d config debug-sa (run amavisd-new stop first) and verify SpamAssassin is locating all of its rule sets in /var/lib/spamassassin/<SA version>. You should also run:
su amavis -c 'spamassassin --lint'
after an update. You should be aware you must reload amavisd-new after this update in order for the new rules to be used. It is important that sa-update completes without error:
/etc/init.d/amavis restart
There are hundreds of SpamAssassin rules that help decide what is spam and what is not. I created a script to help us automatically update the rules:
cd /usr/sbin
Assuming the script ran without error, add a crontab entry:
crontab -e
Change the MM below with a number between 1 and 59 and insert (on the first available blank line):
MM 3 * * 7 /usr/sbin/sa-update.sh
I only run that once a week because rules really don't change that often. While we are at it, have razor discover its servers once a week:
2 2 * * 3 su amavis -c '/usr/bin/razor-admin -discover'
Save and exit the file. Note: during the time amavisd-new is restarting, mail cannot be delivered to it. Postfix will complain "connect to localhost[127.0.0.1]: Connection refused". Postfix will defer this mail (for about 15 minutes). To speed things up, an impatient person may run 'postfix flush' to flush the deferred queue, but I would not. |
With SpamAssassin version 3.2 or newer, we can optionally compile some body rules so they execute faster.
Start by running sa-compile for the first time and check for errors:
sa-compile
If it looks like it didn't crash:
vi /etc/spamassassin/v320.pre
To enable the ability to use compiled rules, uncomment the line:
# loadplugin Mail::SpamAssassin::Plugin::Rule2XSBody
Save and exit the file, then run --lint:
su amavis -c 'spamassassin --lint'
Now grab a script that will run sa-compile once a week:
cd /etc/cron.weekly
Run the script. If it is working correctly, it should take a while, there should be no output and amavisd-new should get reloaded. The script does require that sa-compile has ran at least once before. If you tail the mail.log: tail -50 /var/log/mail.log you should see where amavisd-new was reloaded:
./sa-compile-weekly
|
chown -R amavis:amavis /var/lib/amavis
|
cd /var/lib/amavis
|
chown -R amavis:amavis /var/lib/amavis
|
sa-learn --ham /path/to/hamfiles
works on files that reside on the spamfilter. We don't keep mail on the spamfilter
however. This problem can be solved by using your email client (MUA) to individually
save messages in .EML format. Look for this option among the menu choices or 'Save As'. Edit
a sample .EML file to insure the file looks like plain text. If it is full of
garbage characters, then it cannot be used. Use WinSCP to copy your ham collection to
an empty folder on your spamfilter. Then run sa-learn. Pick messages that
have some substance to them so the database has something to work with. Use this
especially when you receive a message that is tagged as spam, but is in fact ham.
Autolearning (bayes_auto_learn) is turned on by default so the system will have no problem gathering
plenty of spam. I suggest you only feed it additional examples of ham to begin with.
In the future you will want to feed it samples of low scoring spam.
cd /usr/local/src
Change to the dcc subdirectory by using the [tab] key command completion shortcut as shown, then ./configure: cd dcc-dccproc- [tab][enter]
./configure --with-uid=amavis && make && make install
The double ampersands let you run those 3 commands on one line, and if a command fails, then subsequent commands will not run. You will see 'done' if all goes well. Place a link to cron-dccd in our path:
cd
Update file ownership:
chown -R amavis:amavis /var/dcc
Test our installation with:
cdcc info
We should get 'requests ok' from the servers (but 'not answering' from 127.0.0.1 is expected). The instructions say to run cron-dccd each day to clean things up, so we will do that.
crontab -e
and insert (on the next available blank line):
43 11 * * * /usr/bin/cron-dccd
Make sure you have a carriage return at the end of the line, then save the file. |
su amavis -c 'spamassassin -D </var/lib/amavis/sample-spam.txt'
|
/etc/spamassassin/local.cf and add an entry to disable the offending party; for example:
Optional to enable dccifd:
vi /etc/spamassassin/local.cf
and insert:
dcc_home /var/dcc
save and exit, then:
vi /var/dcc/dcc_conf
and change
DCCIFD_ENABLE=off
to:
DCCIFD_ENABLE=on
Then change:
DBCLEAN_LOGDAYS=14
to:
DBCLEAN_LOGDAYS=1
save and exit. If you choose to allow logging, cron-dccd should delete old log files when it runs. Keep your eye on the files that accumulate in the /var/dcc/log directory. It's your choice, but I personally don't want to monitor the DCC logs, so I turn off logging altogether by deleting the log directory and commenting out the logdir entry in dcc_conf:
rm -r /var/dcc/logand comment out:
DCCIFD_LOGDIR="$DCCM_LOGDIR"
We will use a supplied script (rcDCC) to automatically start dccifd when we boot up:
cp /var/dcc/libexec/rcDCC /etc/init.d/adcc
Because we enabled dccifd in dcc_conf, we can start up dccifd by running the script:
/etc/init.d/adcc start
You can expect a few error messages when dccifd starts up, you can ignore these three: find: /etc/rc.d: No such file or directory log thresholds set with -t but no -l directory no -l directory prevents per-user logging with -U Now test that SpamAssassin finds dccifd:
su amavis -c 'spamassassin -D dcc </var/lib/amavis/sample-spam.txt' 2>&1 | grep dccifd
You should see: dbg: dcc: dccifd got response:
|
/etc/resolv.conf. If you
choose not to use a local DNS cache then at
least use a real DNS server as your primary. I have seen
SpamAssassin time out on RBL lookups if it cannot perform DNS queries quickly
enough. This can have a big effect on the final spam score.
I will not pretend that I understand the intricacies of the bind9
program that we will install. We will configure bind9 to be a caching only
name server (with the option of forwarding requests to another server).
You may also consider providing the service we install on this machine
to other machines on your network. Note that you will need to modify
our local firewall (iptables) if you choose to provide this service to
other machines:
iptables -A FIREWALL -p udp -m udp --dport 53 -j ACCEPT
iptables -A FIREWALL -p tcp -m tcp --dport 53 -j ACCEPT
iptables -A FIREWALL -p udp -m udp -s 222.222.222.222/24 --dport 53 -j ACCEPT
iptables -A FIREWALL -p tcp -m tcp -s 222.222.222.222/24 --dport 53 -j ACCEPT
We will install version 9.5.1 of bind9:
cd
For security reasons we want to run BIND chrooted so we will perform the following steps:
/etc/init.d/bind9 stop
Edit the file /etc/default/bind9 so that the daemon will run as the unprivileged user 'bind', chrooted to /var/lib/named:
vi /etc/default/bind9
Modify the line: OPTIONS="-u bind" so that it reads:
OPTIONS="-u bind -t /var/lib/named"
Create the necessary directories under /var/lib:
mkdir -p /var/lib/named/etc
Then move the config directory from /etc to /var/lib/named/etc:
mv /etc/bind /var/lib/named/etc
Create a symlink to the new config directory from the old location (to avoid problems if bind is upgraded in the future):
ln -s /var/lib/named/etc/bind /etc/bind
Make null and random devices, fix permissions of the directories and create a needed file:
mknod /var/lib/named/dev/null c 1 3
We can start up bind9 at this point:
/etc/init.d/bind9 start
Let's see if the service is running:
lsof -i | grep :domain
It is also imperative that after each change we make, we look in our syslog to see if bind9 reported any errors:
tail -27 /var/log/syslog
We are setting up bind9 as a local caching only name server (later you can optionally configure it as a forwarding server). Here we add some additional security measures that prevent unauthorized machines from using our name server:
vi /etc/bind/named.conf.options
On the line below "directory" we want to add a line that restricts use of our name server to the network our spamfilter is on. Place a [Tab] in front of the entry so it lines up with the other entries. You can add more than one network here if you like. Place a ";" (semicolon) after each network. Note that if you actually want to allow other clients to connect to our name server, as explained in the notes above you would also have to modify IP tables to allow this:
allow-query {222.222.222.222/24;};
We need to suppress some logging:
vi /etc/bind/named.conf
And insert (below the first set of comments}:
logging {
Save and exit the file, then I would restart bind9 and check that it is running:
/etc/init.d/bind9 restart
We will get a number of 'RFC 1918 response' related entries in our log unless we include the RFC 1918 zones:
vi /etc/bind/named.conf.local
Remove the comment marks "// " from the beginning of this option:
// include "/etc/bind/zones.rfc1918";
Optionally configure bind9 as a forwarding server. Bind9 as we have it configured now will first query the root servers for hints when needed. There are advantages and disadvantages in doing this. RBL lookups like spamhaus.org monitor usage to their site and may limit the number of connections per day. If you forward DNS requests, they are monitoring the connection of the server you are forwarding to as opposed to your server. Also, ClamAV uses DNS to know when new updates are available. The server you forward to may cache these records and as a result the records may become stale. Try your setup without using forwarding first. If you use forwarding, it is absolutely imperative that any name servers listed here are known to work from our spamfilter. These will almost certainly be the primary and secondary servers you currently have configured in /etc/resolv.conf (not 127.0.0.1, and not the IP address of the local machine) or your ISP's servers. However, they should preferably point to real name servers and not a DNS proxy like your Linksys broadband router or other gateway device (unless that proxy does not allow proper access to real name servers outside your network - which is sometimes the case). Add the 'forwarders' entry just below the 'allow-query' entry we just made:
vi /etc/bind/named.conf.options
and add:
forwarders {444.444.444.444; 555.555.555.555;};
To never query the root servers, optionally add (personally I do this when using a forwarder):
forward only;
Save and exit the file, then once again I would restart bind9 and check that it is running:
/etc/init.d/bind9 restart
And once again, check for errors:
tail -27 /var/log/syslog
Once it is determined bind9 is functioning, you can change the primary nameserver in /etc/resolv.conf:
vi /etc/resolv.conf
and replace the entry for the primary nameserver (the first one listed):
nameserver 444.444.444.444
to the IP address of this machine (our real IP address, not 127.0.0.1):
nameserver 111.111.111.111
Save and exit the file, then test that we are able to resolve host names:
dig a yahoo.com
You should see valid data (A records that have IP addresses), and the output will also tell you which name server was used to find the information: ;; SERVER: 111.111.111.111#53(111.111.111.111)
Make sure this shows this machines IP address as configured in /etc/resolv.conf. Now we can tell Postfix to use the new name server:
LINUX2
|
reboot
|
tail -f /var/log/mail.log
amavisd-new stop
amavisd-new -d 5 debug-sa
or
amavisd-new debug
for more detail.
amavisd-new -d 5 debug-sa 2>&1 | egrep '(DCC|dcc)'
And here I'm looking for ClamAV related items with amavisd-new debug (don't forget to start amavisd-new after debugging):
amavisd-new -d 5 debug 2>&1 | grep Clam
You can increase the level of detail reported by amavisd-new in the mail.log by
adjusting $log_level in amavisd.conf. Remember to set it back to 0 when finished with
your debug session.
cd /var/mail
less any files you may find there. There may be a file
or two that ended up there before Postfix was configured.
Also try the commands mailq
and qshape (and qshape deferred ) to see if there is
mail stuck in the queue. Use amavisd-new debug
while you are sending mail through the system to help provide clues to the problem.
Open another terminal window and run mailq while the
other window is running amavisd-new debug . If you
made changes to configuration files and want to flush the queue, try
postconf -f and if that does not work try
postsuper -r ALL . See
http://www.postfix.org/postsuper.1.html. Insure that the relay_domains parameter
has been configured correctly. Inspect the /etc/postfix/transport
file for errors, and make sure you run
postmap /etc/postfix/transport every time you make changes.
LINUX2
postfix check
|
Additional anti-UCE settings for our Debian Anti-Spam Anti-Virus Gateway Email Server
|
apt-get update
Then install the most recent clamav and clamav-daemon (from squeeze-updates):
apt-get install clamav clamav-daemon clamav-freshclam
|
vi /etc/amavis/amavisd.conf
To ensure virus scanning is enabled, make sure this line is commented out (like this):
# @bypass_virus_checks_maps = (1); # controls running of anti-virus code
Locate the line:
@av_scanners = (
Ensure these 4 lines are uncommented, and make sure the value after CONTSCAN reads as follows: ['ClamAV-clamd',
\&ask_daemon, ["CONTSCAN {}\n", "/var/run/clamav/clamd.ctl"],
qr/\bOK$/, qr/\bFOUND$/,
qr/^.*?: (?!Infected Archive)(.*) FOUND$/m ],
|
/var/run/clamav/clamd.ctl value shown above must match the LocalSocket
parameter in /etc/clamav/clamd.conf Change it here if necessary to match what is in /etc/clamav/clamd.conf.
/etc/clamav/clamd.conf.
The freshclam daemon is set to check for, and download if necessary,
new virus definitions 24 times per day.
The configuration file
for freshclam is /etc/clamav/freshclam.conf
You can check the log files at
/var/log/clamav/freshclam.log and
/var/log/clamav/clamav.log
The startup script for freshclam is
/etc/init.d/clamav-freshclam
and for clamd it's /etc/init.d/clamav-daemon
You can also research additional clamd.conf configuration options by
running man clamd.conf
Stop and start clamd and amavisd-new:
/etc/init.d/amavis stop
We should test ClamAV. To do so, we can simply watch the mail.log go by as we send the Eicar test virus through the system (you will need to temporarily disable the real time virus scanner on your system). Additional instructions listed below.
tail -f /var/log/mail.log
Don't forget to re-enable your real time scanner. |
tail -f /var/log/mail.log so you can see what happens.
apt-get --purge remove clamav clamav-base clamav-daemon clamav-freshclam libclamav5
@bypass_virus_checks_maps
in /etc/amavis/amavisd.conf to disable virus scanning (or
go shopping for another antivirus vendor).
Also: make sure everything works AFTER you reboot. Don't leave ClamAV in a
non-functional state if you have virus scanning enabled. Amavisd-new will not work properly.
Keep an eye on /var/log/clamav/freshclam.log
and /var/log/clamav/clamav.log. You need
to look for error messages in these files. You may have an error or two when the
program is first installed; this is probably OK and may be due to things happening
out of sequence. Check the logs for a couple days and make sure the database
updates do not fail and that Clamd is notified of updates.
Optionally use additional anti-phishing and scam signatures. This setup
uses Bill Landry's clamav-unofficial-sigs.sh script, version 3.7.1:
apt-get install curl rsync
The script will execute. When it's finished:
ls -l /var/lib/clamav
You will notice the data has been downloaded: -rw-r--r-- 1 clamav clamav 11478 2010-06-06 19:52 bytecode.cvd -rw-r--r-- 1 clamav clamav 2196135 2010-06-06 19:52 daily.cvd -rw-r--r-- 1 clamav clamav 50400 2010-05-27 08:12 honeynet.hdb -rw-r--r-- 1 clamav clamav 3950238 2010-06-05 08:49 junk.ndb -rw-r--r-- 1 clamav clamav 559557 2010-06-06 19:49 jurlbl.ndb -rw-r--r-- 1 clamav clamav 22906487 2010-06-06 19:52 main.cvd -rw-r--r-- 1 clamav clamav 52 2010-06-06 19:52 mirrors.dat -rw-r--r-- 1 clamav clamav 2299236 2010-06-06 09:50 phish.ndb -rw-r--r-- 1 clamav clamav 60727 2010-06-05 08:49 rogue.hdb -rw-r--r-- 1 clamav clamav 1116 2010-05-13 04:49 sanesecurity.ftm -rw-r--r-- 1 clamav clamav 1712518 2010-06-04 12:54 scam.ndb -rw-r--r-- 1 clamav clamav 75068 2010-05-27 08:12 securiteinfobat.hdb -rw-r--r-- 1 clamav clamav 193234 2010-05-27 08:12 securiteinfodos.hdb -rw-r--r-- 1 clamav clamav 53913 2010-05-27 08:12 securiteinfoelf.hdb -rw-r--r-- 1 clamav clamav 225919 2010-06-02 02:53 securiteinfo.hdb -rw-r--r-- 1 clamav clamav 1329399 2010-06-03 02:26 securiteinfohtml.hdb -rw-r--r-- 1 clamav clamav 244083 2010-05-27 08:13 securiteinfooffice.hdb -rw-r--r-- 1 clamav clamav 238856 2010-05-27 08:13 securiteinfopdf.hdb -rw-r--r-- 1 clamav clamav 21106 2010-05-27 08:13 securiteinfosh.hdb -rw-r--r-- 1 clamav clamav 52755 2010-06-06 09:50 spamimg.hdb -rw-r--r-- 1 clamav clamav 866409 2010-06-06 19:45 winnow_malware.hdb -rw-r--r-- 1 clamav clamav 785121 2010-06-06 19:45 winnow_malware_links.ndbNow we add a crontab entry with download attempts performed every 6th hour:
crontab -e
Insert these two entries. Replace MM (minutes) below with a number between 1 and 59:
MM */6 * * * /usr/sbin/clamav-unofficial-sigs.sh
Save and exit the file. The first cron job should run every 6 hours, and the second, every 6 minutes. The clamav-status.sh script will restart clamd after a crash. There is a log file at /var/log/clamav-unofficial-sigs.log and you can read the man page at 'man clamav-unofficial-sigs'. Amavisd-new can treat SaneSecurity/MSRBL/securiteinfo 'viruses' as spam. You just need to add some SpamAssassin rules so they score more than 0.1:
cd /etc/spamassassin
vi /etc/amavis/amavisd.conf
and insert the following near the end of the file, just above the last line that says "1; # insure a defined return value ": @virus_name_to_spam_score_maps = (new_RE( # the order matters! [ qr'^Structured\.(SSN|CreditCardNumber)\b' => 0.1 ], [ qr'^(Heuristics\.)?Phishing\.' => 0.1 ], [ qr'^(Email|HTML)\.Phishing\.(?!.*Sanesecurity)' => 0.1 ], [ qr'^Sanesecurity\.(Malware|Rogue|Trojan)\.' => undef ],# keep as infected [ qr'^Sanesecurity\.' => 0.1 ], [ qr'^Sanesecurity_PhishBar_' => 0 ], [ qr'^Sanesecurity.TestSig_' => 0 ], [ qr'^Email\.Spam\.Bounce(\.[^., ]*)*\.Sanesecurity\.' => 0 ], [ qr'^Email\.Spammail\b' => 0.1 ], [ qr'^MSRBL-(Images|SPAM)\b' => 0.1 ], [ qr'^VX\.Honeypot-SecuriteInfo\.com\.Joke' => 0.1 ], [ qr'^VX\.not-virus_(Hoax|Joke)\..*-SecuriteInfo\.com(\.|\z)' => 0.1 ], [ qr'^Email\.Spam.*-SecuriteInfo\.com(\.|\z)' => 0.1 ], [ qr'^Safebrowsing\.' => 0.1 ], [ qr'^winnow\.(phish|spam)\.' => 0.1 ], [ qr'^INetMsg\.SpamDomain' => 0.1 ], [ qr'^Doppelstern\.(Scam4|Phishing|Junk)' => 0.1 ], [ qr'^ScamNailer\.' => 0.1 ], [ qr'^HTML/Bankish' => 0.1 ], # F-Prot [ qr'-SecuriteInfo\.com(\.|\z)' => undef ], # keep as infected [ qr'^MBL_NA\.UNOFFICIAL' => 0.1 ], # false positives [ qr'^MBL_' => undef ], # keep as infected ));Then restart amavisd-new:
/etc/init.d/amavis restart
FYI, here is a link to the available databases that can configured in /etc/clamav-unofficial-sigs.conf http://sanesecurity.co.uk/databases.htm I suggest you subscribe to the general mailing list http://sanesecurity.co.uk/support.htm |
$virus_quarantine_to = undef;.
|
Insert the floppy, and then head back to your Windows machine.
Or just type this stuff in at the console if it's a long walk: We may have to create a device if it does not exist:
test -e /dev/fd0u1722 || mknod /dev/fd0u1722 b 2 60
Create the mount point:
mkdir /floppy
Format the floppy (insert it first of course):
fdformat /dev/fd0u1722
Create a file system on the floppy (we need one that accepts long file names):
mke2fs /dev/fd0u1722
Mount the floppy:
mount /dev/fd0u1722 /floppy
and copy all these files to it: (Yes you can copy and paste this whole section). Yes I know, working with floppies in *nix is a pain:
cp /etc/fstab /floppy
|
ls -l /floppy
This floppy will not be readable by a Windows machine. I can't repeat this enough: Always unmount the floppy before you remove it: I suggest you have the monitor on at the console so you can see the mess you make if you don't.
umount /floppy
Remove it, label it and store it in a safe place. |
mount /dev/fd0u1722 /floppy
cp /floppy/aliases /etc/aliases
newaliases
cp /floppy/main.cf /etc/postfix/main.cf
cp /floppy/master.cf /etc/postfix/master.cf
cp /floppy/sender_access /etc/postfix/sender_access
postmap /etc/postfix/sender_access
cp /floppy/transport /etc/postfix/transport
postmap /etc/postfix/transport
cp /floppy/virtual /etc/postfix/virtual
postmap /etc/postfix/virtual
cp /floppy/relay_recipients /etc/postfix/relay_recipients
postmap /etc/postfix/relay_recipients
cp /floppy/body_checks /etc/postfix/body_checks
cp /floppy/header_checks /etc/postfix/header_checks
cp /floppy/amavisd.conf /etc/amavis/amavisd.conf
cp /floppy/user_prefs /var/lib/amavis/.spamassassin/user_prefs
cp /floppy/local.cf /etc/spamassassin/local.cf
cp /floppy/razor-agent.conf /var/lib/amavis/.razor/razor-agent.conf
cp /floppy/clamd.conf /etc/clamav/clamd.conf
cp /floppy/freshclam.conf /etc/clamav/freshclam.conf
cp /floppy/sources.list /etc/apt/sources.list
apt-get update
umount /floppy
Stop Postfix and amavisd-new so the bayes files are not written to during the backup:
postfix stop
Start your ftp session (substituting your settings):
ftp -p server.domain.tld
Enter your user name and password as requested, and then make a directory to place our files:
ftp> mkdir sfa (only necessary the first time you do this)
Change to that directory:
ftp> cd sfa
Then simply copy and paste this entire section:
ascii
|
get instead of put to restore a file.
For example: get clamd.conf /etc/clamav/clamd.conflogcheck
apt-get install logcheck logcheck-database
If you would like to change any settings:
vi /etc/logcheck/logcheck.conf
|
su -s /bin/bash -c "/usr/sbin/logcheck" logcheck
less /usr/share/doc/logcheck/README.logcheck /etc/logcheck/ignore.d.server/logcheck and insert
a regular expression of the text you wish logcheck to ignore. For example, I
insertedCRON.*: \(pam_unix\) session opened for userCRON.*: \(pam_unix\) session closed for user
You most likely will not want to be annoyed by every message amavisd-new blocks:
echo "^\w{3} [ :[:digit:]]{11} [._[:alnum:]-]+ amavis\[[[:digit:]]+\]: \([-[:digit:]]+\) (Blocked|Passed)" >> /etc/logcheck/ignore.d.server/amavisd-new
Logcheck will also look for keywords (like "attack") contained in the /etc/logcheck/cracking.d/logcheck file. We can tell logcheck to ignore log entries that contain a hostname such as "attackingthedevil.co.uk" by creating a new file in the appropriate logcheck "ignore" directory and placing that text in it. We create a file because none exist at this point:
echo "attackingthedevil.co.uk" >> /etc/logcheck/cracking.ignore.d/logcheck-postfix
If you removed the DCC log directory as I suggested, dccifd will log an error every time it is called. We want logcheck to ignore those log entries (this is a single command):
echo "stat\(log directory /var/dcc/log\): No such file or directory" >> /etc/logcheck/ignore.d.server/dcc
While we are at it, here are a couple dcc messages we don't care about:
echo ": missing message body" >> /etc/logcheck/ignore.d.server/dcc
and a couple Postfix messages I wish to suppress:
echo "dsn=2.7.0, status=sent \(254 2.7.0 Ok," >>/etc/logcheck/ignore.d.server/postfix
And there is more:
echo "\(su amavis -c '/usr/bin/razor-admin -discover'\)" >> /etc/logcheck/violations.ignore.d/logcheck-cron
|
vi -R /usr/share/doc/logcheck-database/README.logcheck-database.gz
su -s /bin/bash -c "/usr/sbin/logcheck -otd" logcheck
which [program name] or whatis [program name]
or dpkg -l [package name]
Use dpkg and grep to send the list of installed program
files to a file called "progs":
cd
Then use less to view the file:
less /root/progs
Or send it in an email to root:
cat /root/progs | mail -s "sfa installed programs" root
|
crontab -e
And insert at the first available blank line (actually, this report is optional):
30 7 * * * /usr/bin/mailq |/usr/bin/tail |/usr/bin/mail -s "mailq sfa" root
While we are editing crontab, for the forgetful type (forgot that you are not supposed to run 'sa-learn'as root) we will make sure 'amavis' still owns the Bayes and AWL files:
30 17 * * * /bin/chown -R amavis:amavis /var/lib/amavis/.spamassassin
Save and exit |
mailq (or as an alternate) you may
wish to use qshape
vi /etc/cron.d/qshape-cron
And insert (2 lines):
PATH=/usr/sbin
Save and exit. Logcheck will now complain each day, so we need to shut it up:
echo "^\w{3} [ :0-9]{11} [._[:alnum:]-]+ postfix/pickup\[[0-9]+\]: [[:alnum:]]+: uid=[0-4]+ from=<postfix>" >> /etc/logcheck/ignore.d.server/postfix
|
|
For consistency, we are not using the most current version of AIDE.
For a 32-bit machine, download and install from me. Jump ahead for a 64-bit machine:
cd /usr/local/src
For a 64-bit machine, download and install from me:
cd /usr/local/src
The installation will have three input screens, answer them as follows: Daily reports are mailed to root by default. [Ok] Initialize aide database? [No] Before AIDE can be used, you will have to initialize a database. [Ok] |
/usr/bin/aide = the executable program file/etc/aide/aide.conf = the configuration file/etc/cron.daily/aide = a nice script that runs the report
Make a new directory, a convenient place to store the files we want:
mkdir /root/aide
Then copy the files, note that we will rename the report script "report":
cp /usr/bin/aide /root/aide
We remove aide:
apt-get --purge remove aide
then we recreate the log directory and restore the man pages:
mkdir /var/log/aide
|
You can use the WinSCP editor if you prefer:
vi /root/aide/aide.conf
Change:
database=file:/var/lib/aide/aide.db
To:
database=file:/floppy/aide.db
Change:
database_out=file:/var/lib/aide/aide.db.new
To:
database_out=file:/root/aide/aide.db.new
Under Custom Rules, edit Binlib, and remove: +m +c Edit Devices, and remove: +i +g +c under # Kernel, change:
=/boot$ Binlib
to:
/boot Binlib
Comment out the entire section under # Log Files
Under # Check crontabs add:
/etc/cron.d Databases
Save and exit. |
vi /root/aide/report
Change:
PATH="/bin:/usr/bin"
To:
PATH="/floppy:/bin:/usr/bin"
Change:
CONFFILE="/etc/aide/aide.conf"
To:
CONFFILE="/floppy/aide.conf"
Change:
[ -f /usr/bin/aide ] || exit 0
To:
[ -f /floppy/aide ] || exit 0
If you would like to send the report to someone other than root, optionally change:
MAILTO="${MAILTO:-root}"
To something like:
MAILTO="${MAILTO:-someuser@example.com}"
Change:
DATABASE="${DATABASE:-/var/lib/aide/aide.db}"
To:
DATABASE="${DATABASE:-/floppy/aide.db}"
Change:
COMMAND="${COMMAND:-check}"
To:
COMMAND="${COMMAND:-update}"
Change:
aide $AIDEARGS --$COMMAND >"$LOGDIR/$LOGFILE" 2>"$ERRORTMP"
To:
aide $AIDEARGS --config=/floppy/aide.conf --$COMMAND >"$LOGDIR/$LOGFILE" 2>"$ERRORTMP"
Save and exit. |
umount /floppy) then remove it.
Insert a floppy in the drive. We are going to format it, create an ext2 file system on it,
mount it, and then copy the AIDE files to it.
We may have to create a device if it does not exist:
test -e /dev/fd0u1722 || mknod /dev/fd0u1722 b 2 60
Make sure we have a mount point (it may already exist):
mkdir /floppy
Run these one at a time and wait for each command to finish:
fdformat /dev/fd0u1722
mke2fs /dev/fd0u1722
fsck /dev/fd0u1722
mount /dev/fd0u1722 /floppy
Then copy these files over to the floppy:
cp /root/aide/aide /floppy
Wait for the files to copy over (30 seconds). Now we can run the routine that creates the first database. We only need to run this once:
/floppy/aide --config=/floppy/aide.conf --init
This creates aide.db.new in the /root/aide directory, this is the initial database and must be copied to the floppy as aide.db.
cp /root/aide/aide.db.new /floppy/aide.db
Wait long enough (20 seconds) for the file to copy over, and then run the report:
/floppy/report
|
cat /var/log/aide/error.log
Now you have to write protect the floppy disk. This is the most important part.
umount /floppy
Then pull out the disk and push up the write protect tab. Reinsert the floppy, and mount it again:
mount /dev/fd0u1722 /floppy
This floppy should remain in the drive all the time. (Unless we need to use the drive for a moment) |
/floppy/report from the command line and
you inspect the report just prior to copying it over to the floppy. If you
left the write protection off the floppy drive for any length of time, it's possible you
can no longer rely on the database. Be paranoid.
crontab -e
And insert:
25 7 * * * /floppy/report
Save and exit |
Change to our home directory:
cd
Unmount the floppy, but leave it in the drive:
umount /floppy
Create an image of the floppy and store it to a file:
dd if=/dev/fd0u1722 of=floppy.img
dd stands for `Copy and Convert' and was renamed to `dd` only because `cc' was reserved for the C compiler. if= input file, of= output file Remove the source disk, insert the destination disk: First, format the new floppy:
fdformat /dev/fd0u1722
Then copy the image to the new floppy:
dd if=floppy.img of=/dev/fd0u1722
Simply use the new disk now. Turn write protect on, then mount the floppy:
mount /dev/fd0u1722 /floppy
|
vi /etc/init.d/startflop
And insert the following text just as it is listed here: #! /bin/sh
#
# very simple startup script
case "$1" in
start)
/usr/bin/test -e /dev/fd0u1722 || /bin/mknod /dev/fd0u1722 b 2 60
/bin/chmod 660 /dev/fd0u1722
/bin/chown root:floppy /dev/fd0u1722
/bin/mount /dev/fd0u1722 /floppy
;;
stop) /bin/umount /floppy
;;
esac
exit 0
Save and exit the file, then make the file executable:
chmod +x /etc/init.d/startflop
Now use this command to enable it and prioritize it:
update-rc.d startflop defaults 80
Now make a symbolic link to it, I will explain why in a moment:
ln -s /etc/init.d/startflop /usr/bin/floppy
|
floppy start
floppy stop
Also to make life easier is a script that copies the aide database to the floppy,
prompting you to insert and remove the floppy as needed. If you already have a file
named 'go', don't overwrite it.
cd
To run the script:
./go
|
df /floppy
|
apt-get install pflogsumm
Then just make sure you have a mailbox (or alias) for root. Root will get a report each morning after 06:25. Hint: cat /etc/crontab. There is one problem with the report. Any email that gets sent to amavisd-new, which includes most mail that isn't rejected at the front door, also comes back from amavisd-new. This means Postfix sees the email twice. So the report lists them twice. For those that are interested, there are a couple scripts out there that pre-process the log files to prevent reporting amavis entries: http://www.gufonero.com/postfix/prepflog.html and http://classic-web.archive.org/web/20080313161349/www.caspergasper.com/spam.shtml |
Mailgraph is optional:
apt-get install mailgraph
Then we modify one setting:
vi /etc/default/mailgraph
Change IGNORE_LOCALHOST=false to:
IGNORE_LOCALHOST=true
Wait a couple minutes, then restart Mailgraph:
/etc/init.d/mailgraph restart
Now you can browse to the graph: http://sfa.example.com/cgi-bin/mailgraph.cgi or http://111.111.111.111/cgi-bin/mailgraph.cgi |
/etc/postfix/sender_access
that can be used to blacklist senders. We created
/etc/postfix/header_checks and /etc/postfix/body_checks
that can be used for content filtering and I provided links to some examples.
The files themselves also provide examples. When we were editing
/etc/amavis/amavisd.conf you noticed sections that dealt with
whitelisting and blacklisting. It is recommended you do "soft" whitelisting
and blacklisting by adding entries to the @score_sender_maps section of amavisd.conf.
Add your entries in the same section that 'nobody@cert.org' => -3.0, is
listed. Negative scores will be subtracted from the overall spam score, and positive
scores will be added.
postfix reload
/etc/init.d/postfix restart
postfix stop
postfix start
/etc/init.d/amavis stop
/etc/init.d/amavis start
amavisd-new stop
amavisd-new start
as does this:
amavisd-new reload
postsuper -r ALL
perldoc Mail::SpamAssassin::Conf
bayes_path /var/lib/amavis/.spamassassin/bayes lock_method flock # # We need stuff from these senders, and they tend to get marked as spam. # We want to whitelist our close business partners. # We subscribe to industry specific newsletters and whitelist them also. # Later we manually feed these to Bayes as ham. whitelist_from spambin@example.com whitelist_from *@generalmotors.com whitelist_from *.usanewstoday.com # # We need stuff from autonetamerica and the Lottery and it always gets marked as spam. # So we will create custom rules that let these particular subject lines reduce the score. header AUTONETAMERICA Subject =~ /Auto Net America/ score AUTONETAMERICA -5.000 header YOURLOTTERY Subject =~ /Your Lottery Results!/ score YOURLOTTERY -5.000 # # We change the scores on a few standard tests - these are just examples score RAZOR2_CF_RANGE_51_100 0.500 score URIBL_WS_SURBL 2.000 score URIBL_PH_SURBL 2.500 score RCVD_IN_SORBS_HTTP 1.000 score RCVD_IN_SBL 1.000 score RCVD_IN_NJABL_PROXY 1.000 score RCVD_IN_SORBS_MISC 0.500 score RCVD_IN_BL_SPAMCOP_NET 2.000 score RCVD_IN_NJABL_SPAM 2.200 # # use_auto_whitelist 0 # uncomment to disable auto-whitelist - a number of people recommend NOT using auto-whitelist.
spamassassin --lint after adding any new rules or
changing anything in local.cf.
/etc/spamassassin/local.cf file is used to
configure SpamAssassin site wide but in our case,
editing /var/lib/amavis/.spamassassin/user_prefs
would have a similar effect. However, certain global SpamAssassin settings will
have no effect if placed in user_prefs, therefore you only need to maintain local.cf.
I also want to mention that the /var/lib/amavis/.spamassassin/bayes_seen file grows forever.
It keeps track of messages it has already learn, so it does not learn the same message over and over.
Every few months, I suggest shutting down amavisd-new, deleting the file and restarting amavisd-new.
SpamAssassin will recreate the file as needed.
/etc/aliases
/etc/postfix/main.cf
/etc/postfix/master.cf
/etc/postfix/sender_access
/etc/postfix/transport
/etc/postfix/virtual
/etc/postfix/relay_recipients
/etc/postfix/body_checks
/etc/postfix/header_checks
/etc/amavis/amavisd.conf
/var/lib/amavis/.spamassassin/user_prefs
/etc/spamassassin/local.cf
/var/lib/amavis/.razor/razor-agent.conf
/etc/clamav/clamd.conf
/etc/apt/preferences
/etc/apt/sources.list
df
fdisk -l /dev/hda or /dev/sda
postsuper -d <ID number>
postsuper -d ALL deferred
This website was created for the author's personal use and entertainment. There is absolutely no warranty. Use entirely at your own risk. Any information contained herein is freely available elsewhere and simply reinterpreted, or more likely misinterpreted, and cannot be assumed to be accurate. There are mistakes in this website and there may or may not be any effort to correct those mistakes in the future. The author accepts no responsibility for any loss or damage caused by the use, lack of use, or misuse, of information contained in this website. Where links are provided to other websites, the author accepts no responsibility and shall not be liable, either directly or indirectly for the content, legality, accuracy, reliability, suitability, quality or decency of content, information, product, advice or services provided by and contained in those sites. Downloading any information from the Internet is done at your own risk, and the risk can be substantial. You knew that, right? All trademarks are the property of their respective owners.